AWS Permissions¶
Before standing up a Threeport control plane in AWS using the eks
provider, ensure you have the required IAM permissions set for your AWS user.
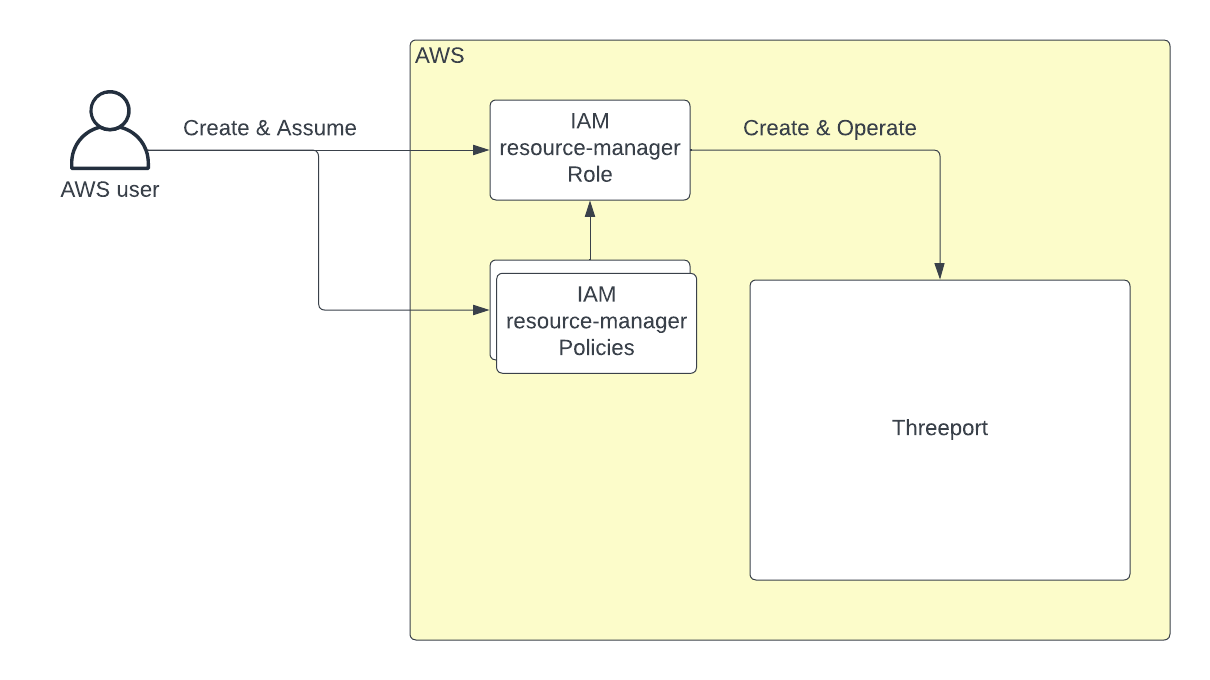
To install Threeport using tptctl up, an AWS user first creates a new "resource-manager" role
and two policies for that role. The AWS user then assumes that role in order to
create and operate Threeport. Therefore an AWS user needs the following
permissions to install and manage Threeport:
- Create and manage IAM roles
- Create and manage IAM permissions
- Assume that role for installing Threeport
If you don't have those permissions, you will need someone else on your AWS account to grant you that access. The following instructions are for that user on AWS to grant access to another user to manage Threeport installations.
Threeport Resource Manager Permissions¶
To see the permissions available to the resource-manager role that manages Threeport, see the AssumeAnyRolePolicyDocument and ResourceManagerPolicyDocument in the Threeport source code.
Prerequisites¶
The instructions below require:
Set Environment Variables¶
Following are the values we will need to set up access for another user to manage Threeport.
Set the user name for the user being granted access to manage Threeport:
1 | |
Set your AWS account ID:
1 | |
Set the names of the group and policy for Threeport admins. These are arbitrary and can be changed:
1 2 | |
Create a Threeport Admin Policy¶
The following command will generate the policy document for your ThreeportAdmin users and write it to your working directory.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 | |
Create the policy in AWS and capture the policy ARN:
1 2 3 4 5 6 | |
Create a User Group¶
Create a group for managing Threeport instances:
1 2 | |
Attach Policy to User Group¶
1 2 3 | |
Add Threeport Admin User to the User Group¶
1 2 3 | |
You can now add more users to that group if need be:
1 2 3 4 | |
Clean Up¶
Remove the Threeport admin policy document file:
1 | |